Esta página ha sido traducida de manera automática y puede contener errores
Protege la seguridad de tu sistema y la privacidad de tus datos
DHIS2 proporciona las herramientas y funciones estándar del sector que necesitas para mantener un sistema de información seguro, poniendo los datos a disposición de los usuarios y restringiendo al mismo tiempo el acceso no autorizado. Con DHIS2 puedes configurar un sistema que respete la privacidad y la confidencialidad y apoye el cumplimiento de las leyes locales y nacionales de privacidad y protección de datos, como la GDPR.
Enlaces directos al contenido de la página
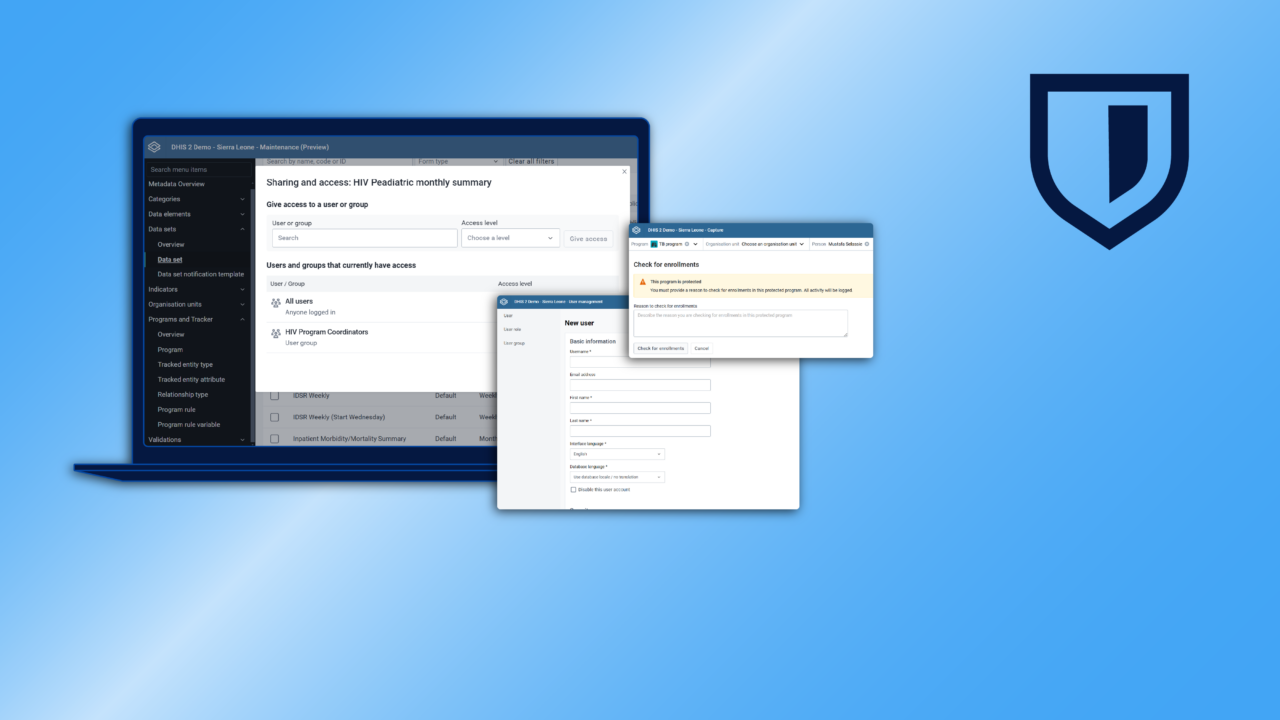
Controlar el acceso y los permisos de los usuarios
DHIS2 incluye diversas herramientas integradas para gestionar el acceso de los usuarios. A través de la aplicación Usuarios, DHIS2 cuenta con un sólido sistema de Control de Acceso Basado en Roles (RABC), que te permite definir los privilegios de acceso por rol de usuario, grupo de usuarios e incluso por usuario. Puedes especificar exactamente a qué unidades organizativas de la jerarquía de tu organización deben acceder los usuarios de DHIS2 para la captura de datos, la búsqueda y la visualización.
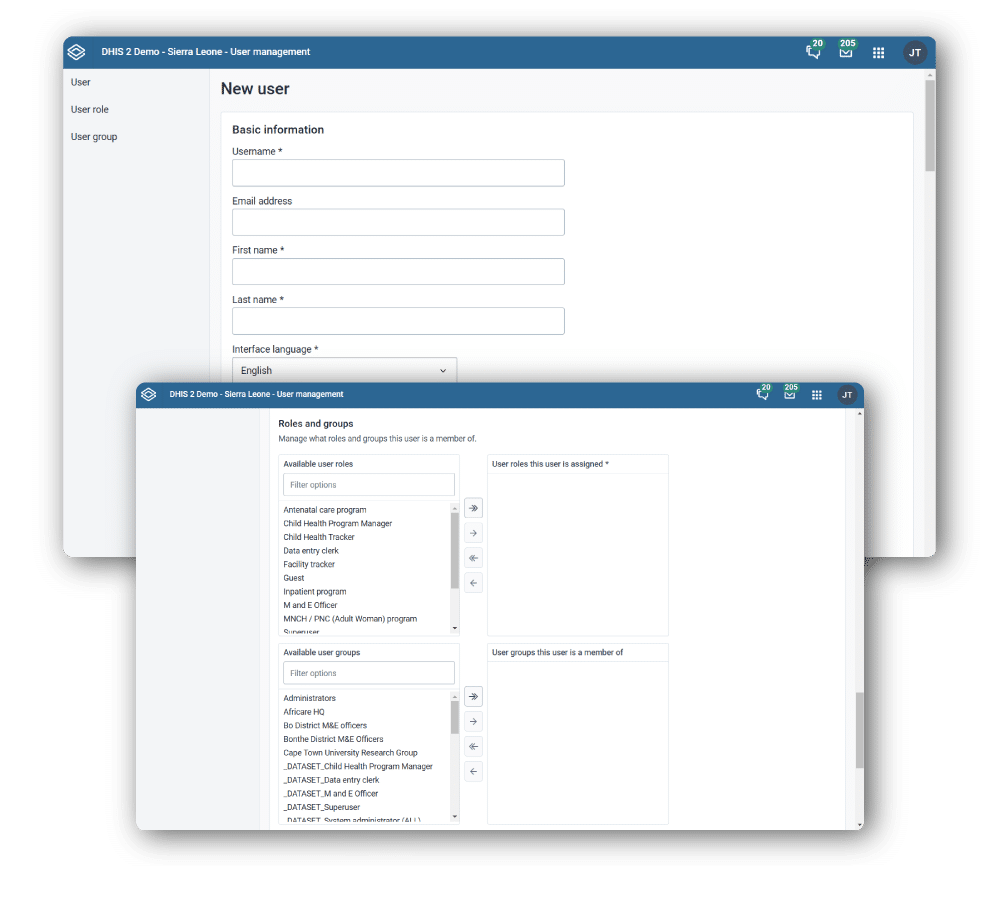
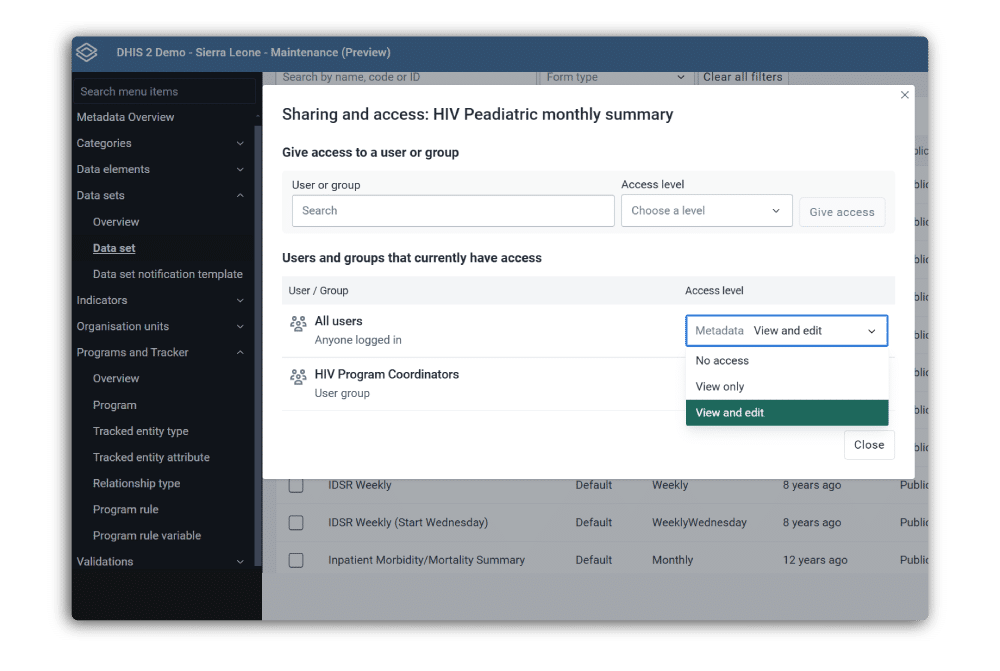
Asignar configuración de uso compartido para datos y metadatos
Además de controlar los permisos a nivel de usuario, DHIS2 también admite el control de acceso granular a objetos de metadatos individuales y a sus datos asociados mediante la configuración de uso compartido. Configurar estos ajustes a través de la Aplicación Mantenimiento te permite conceder permisos de lectura y escritura sólo a determinados usuarios y grupos de usuarios para restringir el acceso a información sensible.
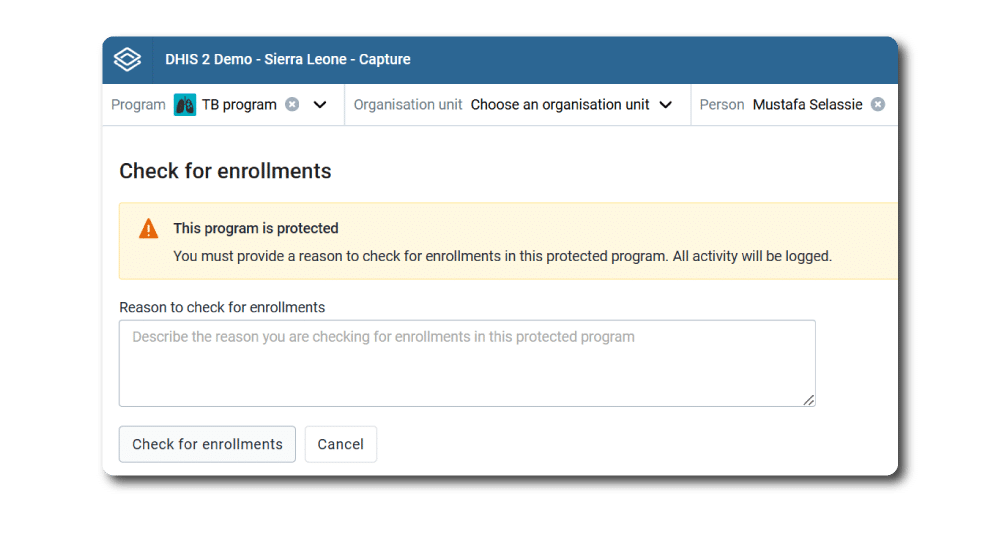
Conceder excepciones a las restricciones de acceso de forma segura
Los controles de acceso ayudan a mantener seguros los sistemas, pero cuando se interponen en el camino de las personas que hacen su trabajo, pueden dar lugar a prácticas que creen riesgos de seguridad adicionales. Por esta razón, DHIS2 proporciona funcionalidades que ayudan a sortear las barreras habituales que pueden surgir sin comprometer la seguridad del sistema. Por ejemplo, DHIS2 admite un modo operativo en el que los usuarios con privilegios pueden hacerse pasar por otros usuarios y realizar determinadas acciones en su nombre. En los programas Tracker, en los que los usuarios pueden necesitar buscar personas que no están asociadas a su unidad organizativa (y que, por tanto, normalmente estarían fuera de su capacidad de ver o editar), DHIS2 puede configurarse para permitir a los usuarios «romper el cristal» y acceder a estos registros, pero sólo después de introducir una razón para la operación, que luego es registrada por el servicio de auditoría.
Mantén tu sistema seguro con autenticación multifactor o externa
Con frecuencia, las organizaciones recomiendan o exigen el uso de la autenticación de dos factores para reducir el riesgo de acceso no autorizado por pérdida o robo de contraseñas. DHIS2 admite la autenticación multifactor utilizando una app autenticadora como segundo factor, así como servicios de autenticación externos a través de servidores de directorio compatibles con LDAP (Active Directory, OpenLDAP, etc.).
Agiliza el inicio de sesión seguro con el inicio de sesión único
En el lugar de trabajo moderno, los usuarios de ordenador a menudo tienen que iniciar sesión en varios sistemas de software y sitios web en el transcurso de un día cualquiera, lo que conduce a un conjunto cada vez mayor de contraseñas que deben memorizarse y mantenerse seguras. Para facilitar el proceso de inicio de sesión y reducir los riesgos de seguridad, DHIS2 admite el inicio de sesión único mediante OpenID Connect (OIDC), lo que te permite permitir a los usuarios iniciar sesión en DHIS2 automáticamente utilizando sus credenciales de otro sistema compatible.
Desactiva automáticamente las cuentas inactivas y caducadas
El número de usuarios de un sistema DHIS2 puede ascender a cientos de miles, lo que dificulta la gestión a largo plazo de las cuentas de usuario individuales y contribuye al riesgo de que los usuarios sigan teniendo acceso a los datos después de haber cambiado de función o abandonado la organización. Para ayudar a gestionar esto, DHIS2 te permite establecer fechas de caducidad para las cuentas de usuario y desactivar automáticamente a los usuarios inactivos para evitar el acceso no autorizado al sistema.
Control flexible de la configuración del servidor y la base de datos
Hay muchas formas de aprovisionar un sistema DHIS2, por ejemplo en distintos entornos físicos (en las instalaciones, en coubicación, en nube privada, en nube pública), utilizando distintos sistemas operativos y enfoques técnicos. Existen diferentes conjuntos detallados de controles de seguridad que pueden y deben aplicarse en función de estas opciones de diseño. La flexibilidad de DHIS2 te da un control total sobre la configuración de tu sistema y tu entorno de alojamiento.
Cifrar los datos DHIS2 en dispositivos móviles
Android App Captura es una solución popular para recopilar datos en dispositivos móviles. Sin embargo, esto crea un riesgo adicional de acceso no autorizado a los datos sensibles que se hayan recogido o descargado del servidor DHIS2, en caso de pérdida o robo del dispositivo. Mediante la Aplicación de Configuración de Android, un administrador del sistema puede forzar a todas las aplicaciones DHIS2 Android a utilizar el cifrado local de la base de datos, garantizando que los datos sean inaccesibles para usuarios no autorizados, incluso si acceden al dispositivo físico.
Sigue los cambios en tu sistema DHIS2
DHIS2 proporciona una funcionalidad opcional de registro de cambios (activada por defecto) que escribe entradas en los registros de cambios cuando se modifican ciertas entidades en el sistema. Esto incluye los cambios en los valores de los datos agregados, así como -para los programas Tracker- los cambios en las instancias del programa, los elementos de propiedad temporal del programa, los valores de los atributos de la entidad rastreada y los valores de los datos de la entidad rastreada. Estos registros de cambios te permiten ver los cambios que se han realizado en los datos, y qué usuarios han realizado el cambio, lo que ayuda a mantener la integridad de los datos y la responsabilidad. DHIS2 también admite registros de auditoría como función opcional, que pueden utilizarse para registrar las operaciones sensibles realizadas por los usuarios en un registro de auditoría en el almacén de archivos o en la base de datos.
Cumplimiento de las normas de privacidad locales e internacionales
DHIS2 te proporciona las herramientas que necesitas para poder implementar tu sistema DHIS2 de acuerdo con los requisitos de cumplimiento -que, en última instancia, se basan en cómo se aloja y configura el sistema en cada caso-, como GDPR, HIPAA, ISO-27000 y otras normas de privacidad y seguridad de datos.
Las actualizaciones de software te ayudan a mantener seguro tu sistema DHIS2
La organización del software central de DHIS2 incluye un equipo de seguridad dedicado a identificar y mitigar las vulnerabilidades de la plataforma DHIS2. El código fuente de DHIS2 se analiza continuamente en busca de vulnerabilidades de seguridad de la lista OWASP Top 10 gracias a una variedad de herramientas automatizadas, para garantizar que los errores más comunes se solucionan al principio del proceso de desarrollo, y estamos mejorando continuamente nuestra arquitectura de software, funciones y procesos para minimizar el riesgo para los usuarios y sus datos. Cuando se descubren y solucionan vulnerabilidades, publicamos versiones «hotfix» que se anuncian en DHIS2 Comunidad de Práctica y están disponibles para su descarga inmediata en nuestro sitio web.
Más información sobre las herramientas de seguridad de DHIS2
Utiliza los enlaces siguientes para obtener más información sobre las herramientas integradas de DHIS2 que apoyan la seguridad y la privacidad, explorar nuevas funciones, leer la documentación y descargar las últimas versiones.
Usuarios
La aplicación Usuarios de DHIS2 ofrece un sólido sistema de Control de Acceso Basado en Roles (RABC), que te permite definir los privilegios de acceso por rol, usuario y grupo de usuarios.
Aplicación Mantenimiento
Con la Aplicación Mantenimiento, puedes controlar la configuración de uso compartido de los sets de datos, la visualización y otros objetos de tu sistema DHIS2.
Ajustes de Android
Esta aplicación web te permite controlar los ajustes clave, como la encriptación, de todas las instalaciones de la aplicación móvil Android Captura para tus programas DHIS2.
Recursos para la implementación de sistemas DHIS2 seguros
Consulta estos recursos en línea para obtener directrices y buenas prácticas sobre la implementación de sistemas DHIS2 seguros, así como información actualizada sobre las últimas novedades en materia de seguridad del equipo DHIS2:
También puedes apuntarte a cursos de formación presenciales sobre temas relacionados con la seguridad a través de la Academia DHIS2.