The DHIS2 Annual Conference takes place from 15-18 June 2026! Learn more
Protect your system security and data privacy
DHIS2 provides industry-standard tools and features you need to maintain a secure information system, making data available to users while restricting unauthorized access. With DHIS2 you can configure a system that respects privacy and confidentiality and supports compliance with local and national data privacy and protection laws such as GDPR.
Jump to a section on this page
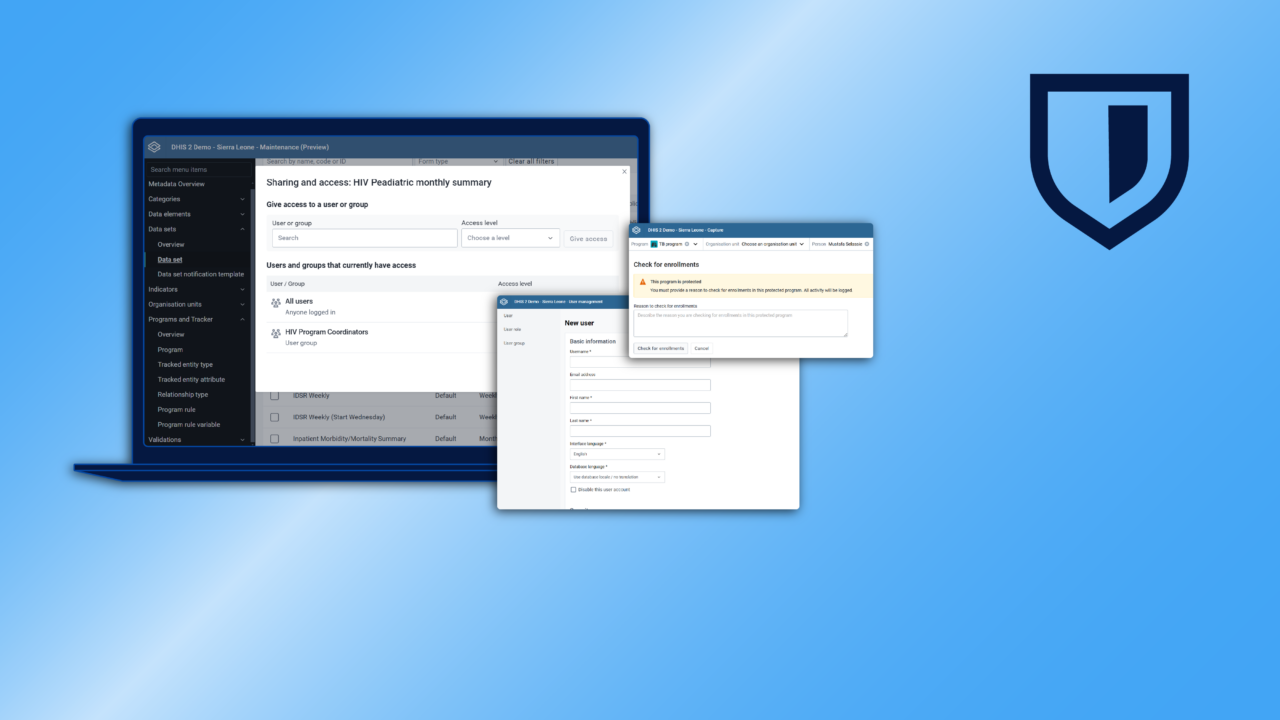
Control user access and permissions
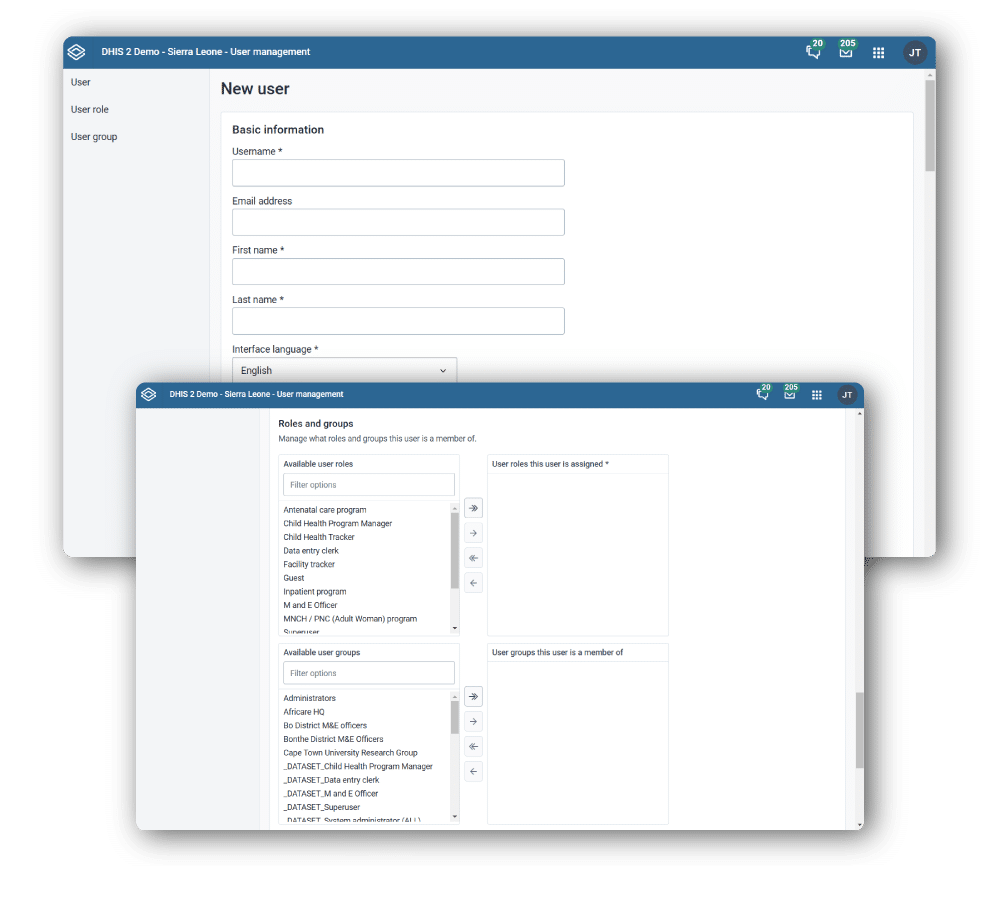
DHIS2 includes a variety of built-in tools for managing user access. Through the Users app, DHIS2 features a robust Role-based Access Control (RABC) system, allowing you to define access privileges per user role, user group, and even on a per user basis. You can specify exactly which organisation units in your organisation hierarchy DHIS2 users should be allowed to access for data capture, search, and visualization.
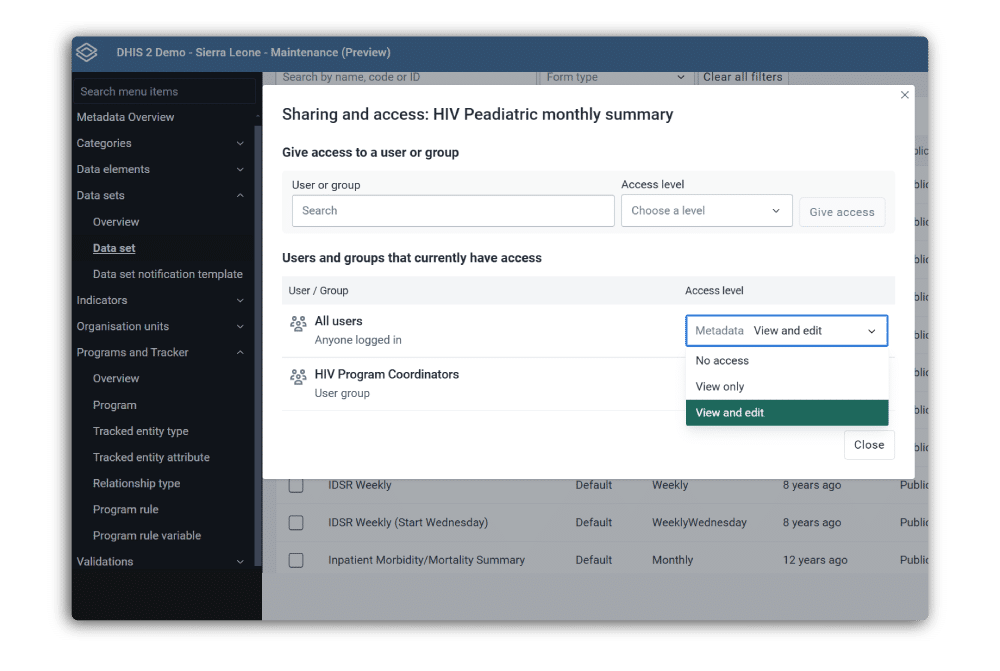
Assign sharing settings for data and metadata
In addition to controlling permissions on a user level, DHIS2 also supports granular access control to individual metadata objects and their associated data through sharing settings. Configuring these settings through the Maintenance app allows you to grant read and write permissions to only certain users and user groups to restrict access to sensitive information.
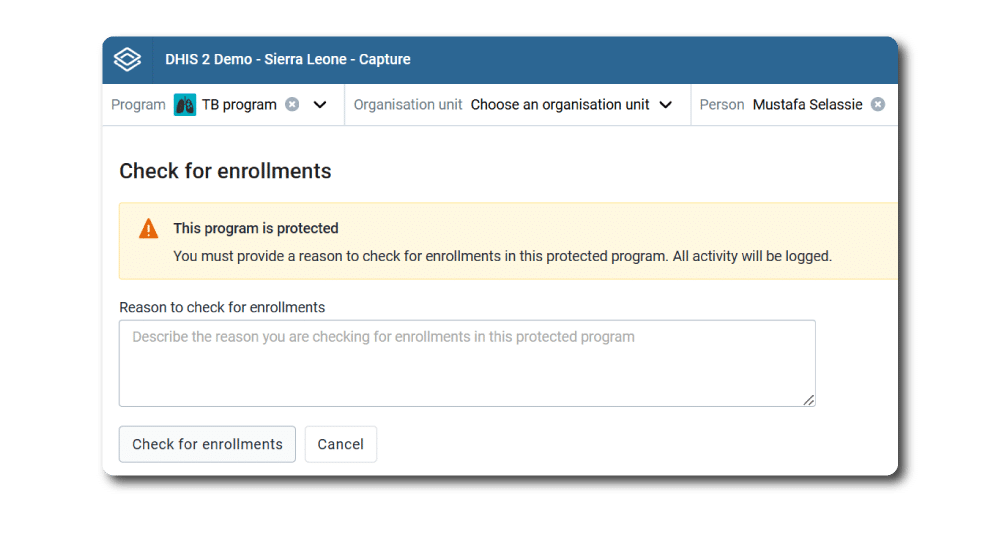
Grant exceptions to access restrictions in a secure way
Access controls help to keep systems secure, but when they get in the way of people doing their jobs, they can potentially result in practices that create additional security risks. For this reason, DHIS2 provides functionalities that help work around common barriers that may occur without compromising system security. For example, DHIS2 supports an operational mode where privileged users can impersonate other users and perform certain actions on their behalf. In Tracker programs, where users may need to search for individuals who are not associated with their organisation unit (and thus would normally be outside of their ability to view or edit), DHIS2 can be configured to allow users to “break the glass” and access these records, but only after entering a reason for the operation, which is then logged by the audit service.
Keep your system secure with multi-factor or external authentication
Use of two-factor authentication is frequently recommended or required by organizations to reduce the risk of unauthorized access due to lost or stolen passwords. DHIS2 supports multi-factor authentication using an authenticator app as a second factor, as well as external authentication services through LDAP-compatible directory servers (Active Directory, OpenLDAP, etc).
Streamline secure login with single sign-on
In the modern workplace, computer users frequently need to sign in to multiple software systems and websites in the course of any given day, which leads to an ever-increasing set of passwords that need to be memorized and kept secure. To make the login process smoother and reduce security risks, DHIS2 supports single sign-on using OpenID Connect (OIDC), allowing you to enable users to login to DHIS2 automatically using their credentials from another compatible system.
Disable inactive and expired accounts automatically
The number of users in a DHIS2 system can number in the hundreds of thousands, making the long-term management of individual user accounts a challenge and contributing to the risk of users continuing to have access to data after they have changed roles or left the organization. To help manage this, DHIS2 lets you set expiration dates for user accounts and automatically disable inactive users to prevent unauthorized system access.
Flexible control of server and database configuration
There are many ways that a DHIS2 system can be provisioned, including on different physical environments (on-premises, co-location, private cloud, public cloud) using different operating systems and technical approaches. There are different detailed sets of security controls which can and should be applied depending on these design choices. The flexibility of DHIS2 gives you complete control over configuring your system setup and hosting environment.
Encrypt DHIS2 data on mobile devices
The Android Capture app is a popular solution for collecting data on mobile devices. However, this creates an additional risk for unauthorized access to sensitive data that has been collected or downloaded from the DHIS2 server, in the event that the device is lost or stolen. Using the Android Settings App, a system administrator can force all DHIS2 Android applications to use local database encryption, ensuring that the data is inaccessible to unauthorized users even if they gain access to the physical device.
Keep track of changes in your DHIS2 system
DHIS2 provides optional changelog functionality (enabled by default) that writes entries to changelogs when certain entities are changed in the system. This includes changes to aggregate data values, as well as–for Tracker programs–changes to program instances, program temporary ownership items, tracked entity attribute values and tracked entity data values. These changelogs allow you to see changes which have been performed to the data, and which users have made the change, helping maintain data integrity and accountability. DHIS2 also supports audit logs as an optional feature, which can be used to log sensitive operations performed by users to an audit log in the filestore or database.
Compliance with local and international privacy standards
DHIS2 provides you with the tools you need to be able to implement your DHIS2 system in accordance with compliance requirements–which are ultimately based on how the system is hosted and configured in each instance–such as GDPR, HIPAA, ISO-27000, and other standards for data privacy and security.
Software updates help you keep your DHIS2 system secure
The DHIS2 core software organization includes a dedicated security team focused on identifying and mitigating vulnerabilities in the DHIS2 platform. DHIS2 source code is continuously analyzed for security vulnerabilities on the OWASP Top 10 list thanks to a variety of automated tools, to ensure most common bugs are addressed early in the development process, and we are continuously improving our software architecture, features and processes to minimize the risk to users and their data. When vulnerabilities are discovered and addressed, we publish “hotfix” releases that are announced on the DHIS2 Community of Practice and available for immediate download on our website.
Learn more about DHIS2 security tools
Use the links below to find out more about DHIS2’s built in tools that support security and privacy, explore new features, read the documentation, and download the latest versions.
Users
The DHIS2 Users app offers a robust Role-based Access Control (RABC) system, allowing you to define access privileges by role, user, and user group.
Maintenance
With the Maintenance app, you can control sharing settings for data sets, visualization, and other objects in your DHIS2 system.
Android Settings
This web app gives you control over key settings such as encryption for all installations of the Android Capture mobile app for your DHIS2 programs.
Resources for implementing secure DHIS2 systems
Check out these online resources for guidelines and best practices on implementing secure DHIS2 systems, and updates on the latest security updates from the DHIS2 team:
You can also sign up for in-person training courses on security-related topics through the DHIS2 Academy.