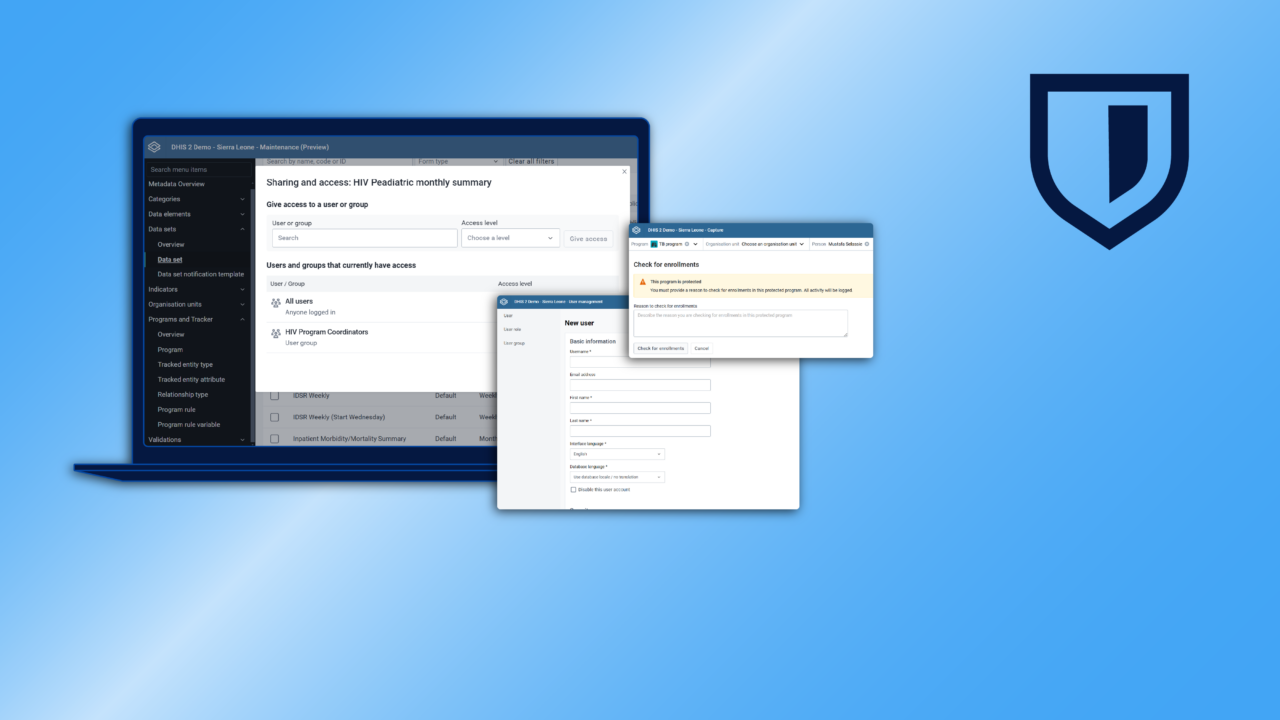
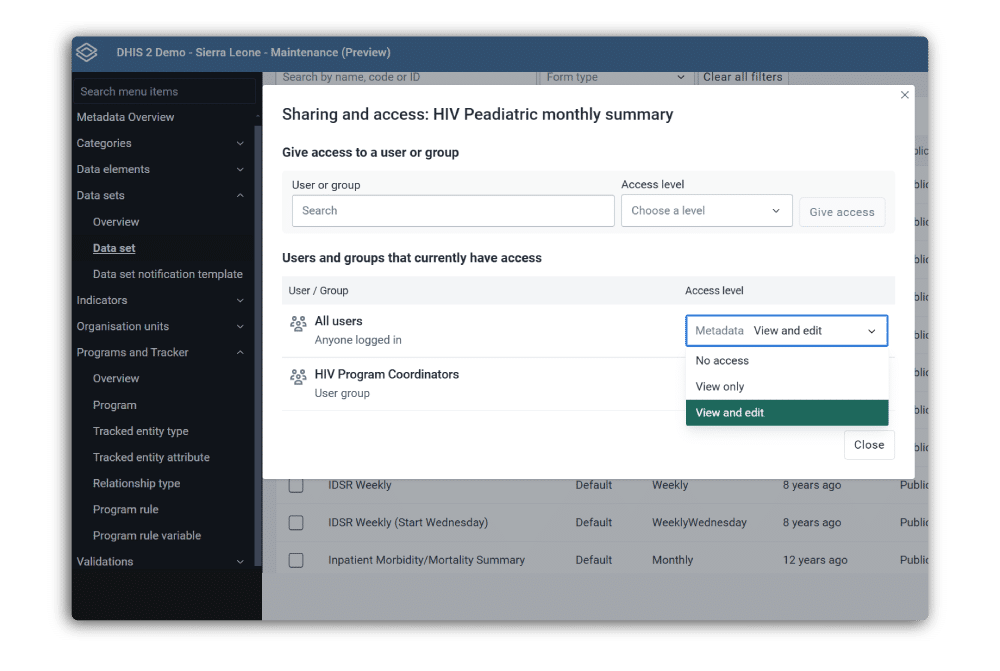
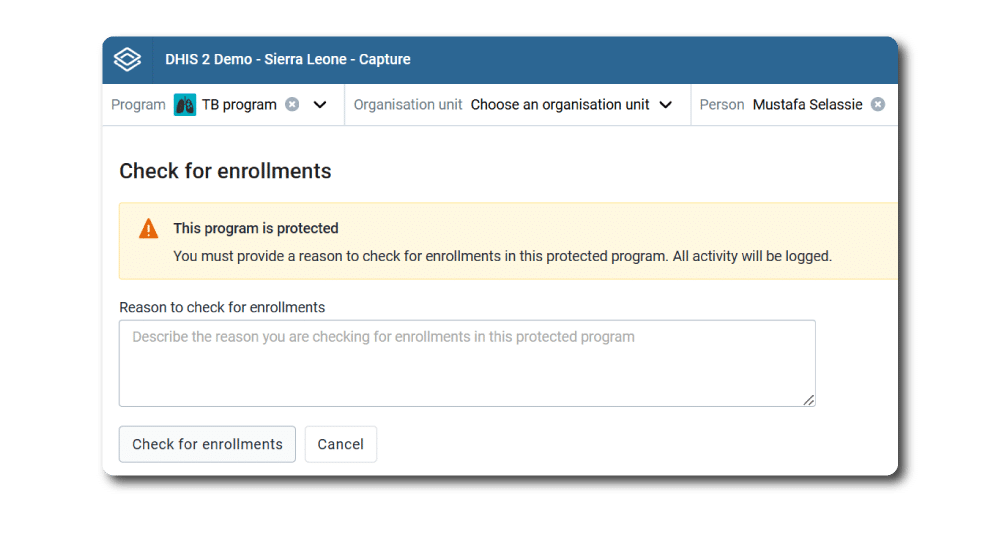
Access controls help to keep systems secure, but when they get in the way of people doing their jobs, they can potentially result in practices that create additional security risks. For this reason, DHIS2 provides functionalities that help work around common barriers that may occur without compromising system security. For example, DHIS2 supports an operational mode where privileged users can impersonate other users and perform certain actions on their behalf. In Tracker programs, where users may need to search for individuals who are not associated with their organisation unit (and thus would normally be outside of their ability to view or edit), DHIS2 can be configured to allow users to “break the glass” and access these records, but only after entering a reason for the operation, which is then logged by the audit service.